Cross-Site Scripting definition
Cross-Site Scripting (XSS) is a prevalent web security vulnerability, enabling attackers to inject malicious scripts into trusted websites, compromising user data and interactions.
What is Cross-Site Scripting?
Cross-Site Scripting, often abbreviated as XSS, is a significant security vulnerability that mostly affects web applications. In an XSS attack, harmful scripts are injected into trusted websites. These malicious scripts can then access sensitive information from users or manipulate their online interactions. XSS attacks come in different forms such as 'reflected', 'stored', and the less common 'DOM-based'. The consequences of these attacks vary from minor annoyances to severe threats like complete account compromise or data theft. As such, understanding and preventing XSS vulnerabilities is critical for maintaining robust web security.
Understanding Different Types of XSS Attacks
To fully comprehend the threat posed by XSS attacks, it's crucial to understand their different types. The most common are 'reflected', 'stored', and 'DOM-based' XSS attacks. Reflected XSS attacks occur when a malicious script is embedded in a URL, which is then reflected off the web server and executed in a user's browser. On the other hand, Stored XSS attacks involve harmful scripts being permanently stored on target servers, making them persistently dangerous for users visiting the affected pages. Lastly, DOM-Based XSS, though less common, manipulates HTML documents directly through Document Object Model (DOM) environments within browsers without any server interaction.
Consequences of Cross-Site Scripting Attacks
The consequences of Cross-Site Scripting attacks can be severe and far-reaching. In their most harmless form, these attacks may cause minor annoyances like unexpected pop-up windows or altered web page content. However, on the more serious end, XSS attacks can result in complete account compromise or data theft. Attackers may gain access to personal information such as passwords, credit card numbers, or other sensitive data. Additionally, they can potentially control your interactions with a website - actions like posting content on your behalf or even altering the site's appearance are possible. This makes XSS attacks a major threat to both individual users and organizations alike.
Best Practices to Prevent XSS Vulnerabilities
Preventing XSS vulnerabilities requires a combination of defensive measures. Firstly, incorporating secure coding practices is essential. This includes input filtering, where all data originating from external sources is scrutinized before being used. Secondly, output escaping, which involves making potentially harmful characters safe for usage, decreases the risk of malicious script execution.
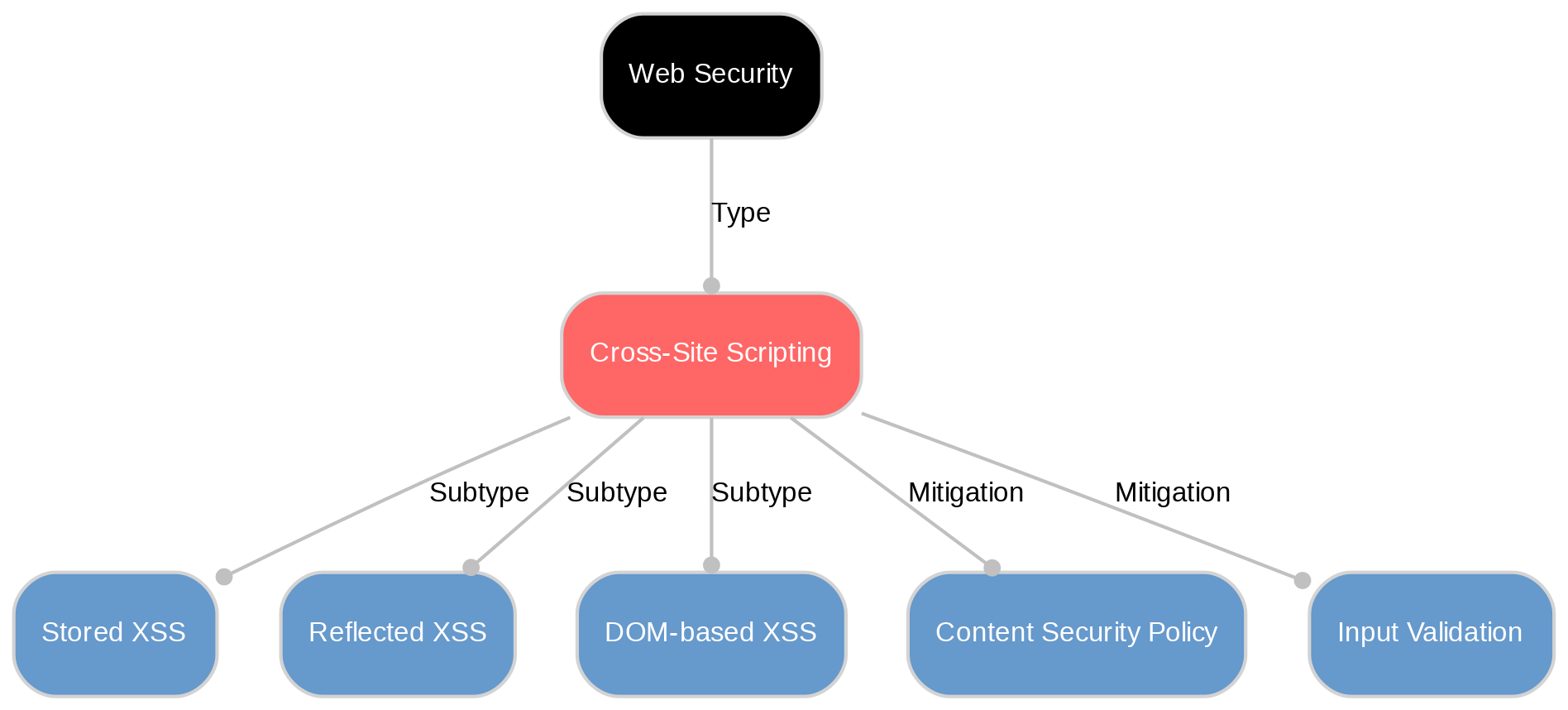
Content Security Policy (CSP), a security standard that helps prevent XSS attacks by controlling which scripts can run on a webpage, should also be utilized. Modern web frameworks often promote good security practices like this.
A crucial defensive technique against XSS attacks is the use of HTML sanitization and output encoding. These techniques ensure that any code received from an untrusted source is rendered harmless before it's executed.
In addition to these precautions, organizations should employ automated tools and services like Sanity that regularly test for and identify potential vulnerabilities in their web applications.
Discover More with Sanity
Now that you've learned about Cross-Site Scripting, why not start exploring what Sanity has to offer? Dive into our platform and see how it can support your content needs.
Last updated: